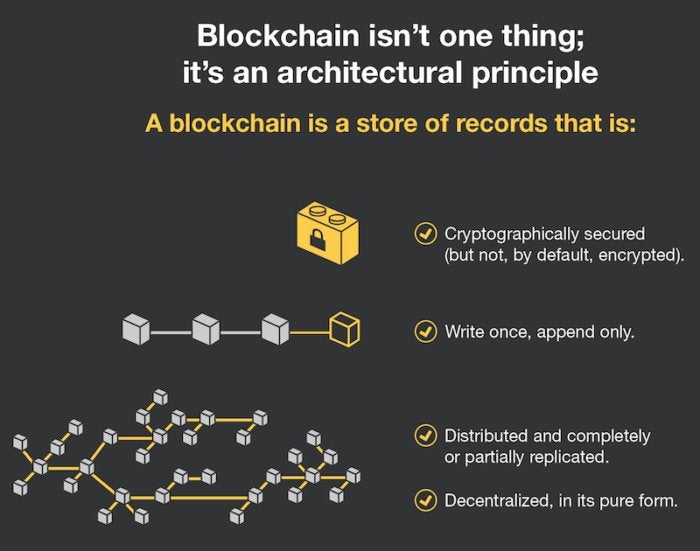
If you know Java, you’re not one of the cool kids any more. Although it is fair to say that most business software is written in Java, the days of paying a premium for a Java developer are long over. So, if you’re a Java developer what’s your next step? One or more of the following languages.
Scala
Scala is like functional Java—if functional Java’s syntax wasn’t kinda cracked. Functional purists aren’t big fans of Scala, but the trek from Java to Scala is short. Moreover, with AI and machine learning becoming the hot topics of the day and Apache Spark being written in Scala, this is kind of an obvious choice.
JavaScript
If you’re a Java developer, statistically you’re probably older than 35—unless you work for a large outsourcing firm. Your last taste of JavaScript was probably that cruddy Netscape thing that they shoved in the browser to make “DHTML” and slapped the word “Java” on because Java was popular (a shortsighted branding decision!).
But JavaScript has changed, and so has server-side software. You already know Java, so you should learn functional constructs. JavaScript has become a server-side and client-side language and is used nearly anywhere you need a “quick fix” scripting language. It’s a good thing to have in your toolkit.
C
If you never learned C, this classic language is back on the rise. Moreover, even if you don’t use it (to, say, program Arduino devices), it will help you understand how Java works and how to debug the big issues when they go wrong, like concurrency issues and race conditions.
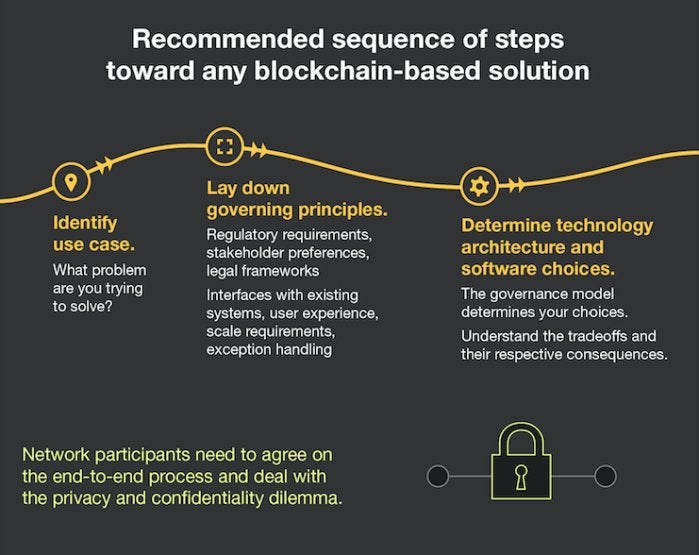
If you know C#, choose from these languages
If you know C# then you’re a ’Softie. But while you were worshipping at the Microsoft house that was built by Gates, the world changed. So you should make yourself more marketable both outside of the Microsoft world and within it by learning one or more of these languages.
JavaScript
Again, this isn’t the JavaScript of old. And it is now used everywhere. JavaScript is also the most accessible and for server-side command-line (CLI) apps, and, no, you don’t have to use that JScript turd that Microsoft plopped out a few years back. There are other, better .Net bindings for JavaScript.
It is also still a good time to try using Node.js or a similar runtime or try to make a pure web app if you’ve been making client apps in C#.
F#
While F# didn’t set the world on fire as predicted, it is still a great way to get totally dirty with functional programming and expose yourself to the data science mindset. If you’re working your way toward AI or machine learning, or if you just want a cleaner way to do complex calculations, then F# is your daddy.
C
You thought Java was going to make this list, didn’t you? No, just like Java developers, C# programmers need to go deeper and understand how the runtime actually works. And that means understanding C. Learn C because it is good for you.
PowerShell or Bash
Clicking around to make things happen is for users. You need to be able to automate all of your mundane tasks. Microsoft’s PowerShell and the Bash terminal available in multiple operating systems are the most widely used tools for such automation.
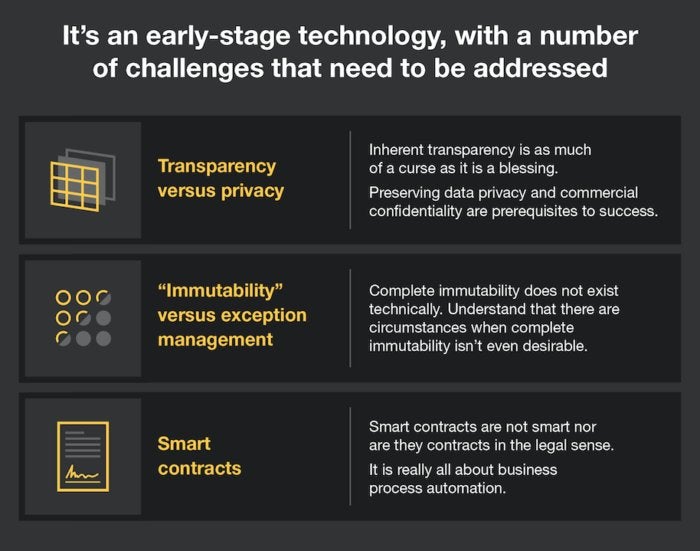
If you know JavaScript, choose from these languages
You put “full-stack developer” on your résumé, didn’t you? But you haven’t really been fooling anyone because you’re a much better front-end developer than back-end. Frankly, it is time to make good on that “full stack” promise.
R
What, you say? Isn’t R for data scientists and statisticians? Yes, but it is also a relatively simple language that can easily generate visualizations with data. Grab that R Studio and take an online class from Harvard or Microsoft if you’re so inclined. (Hint: the Harvard course is more affordable than Microsoft—go figure!)
SQL
You’re a NoSQL guy or gal, so why SQL? Because it is a fair bet that more people know SQL than any other language. It also isn’t going anywhere, and it is a good way to help you think about data in the right way.
Python
Python isn’t simple to learn, but it is easier to learn enough to do something meaningful than, say, Java or Scala. Moreover, the more obvious choice of Ruby is declining in popularity, so I can’t really recommend it because I’m not sure it will be useful in a few years outside of a cult following.
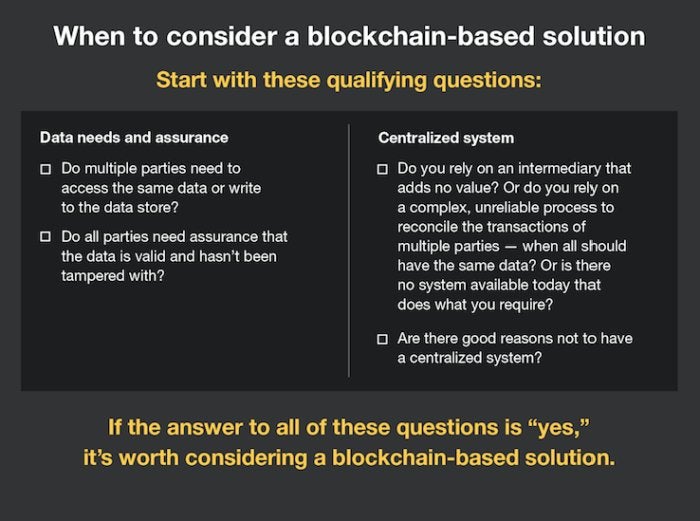
If you know Ruby, choose from these languages
You went to a code bootcamp. You learned Ruby. You probably now realize that you might have wasted your money. Where do you go from here?
JavaScript
You’ve probably already had a taste of JavaScript on the front end. Go deeper and learn JavaScript. Also consider learning Angular or a similar framework with it. Play with Node.js or a similar back-end runtime.
Python
Python is a popular language with the data crowd but you can still do web apps with it. If you want to make yourself more versatile and marketable (read: make more money), learning Python might just be your jumping-off point.
R
I have the same advice for you as I had for JavaScript developers: Learn R, a relatively simple language that allows generating visualizations and changes how you think about data.
If you know C or C++, choose from these languages
If you’re programming in C or C++, you’re doing embedded stuff, drivers, or low-level stuff—or you’re just old. The bottom line is you should learn at least one language with managed memory.
D
Learning D will not help you get a job anywhere, and it may be of little practical use. But it is a convenient way to taste managed memory and all of the “new” concepts without leaving familiar tool chains and losing the C library.
JavaScript
Learn the language of the web: JavaScript. Learn it as a back-end language or as a front-end languages, or both, but learn the language of the web. To learn it correctly these days is to learn it somewhat functionally. D is probably a shorter trek at first.
R
Again, this simple language changes how you think about data. R is also almost immediately useful because you can make visualizations. Surely you have some log data to debug somewhere; this will help.
If you know Perl, choose from these languages
So, your neckbeard is long and you’re still convinced the camel was right and right was wrong or some kinda twisted logic. Text processing isn’t the thing it once was and “look, ma, regex is embedded” isn’t impressing anyone the way it once did. So learn one or more of the following languages.
R
I know I’ve said it before, but R is an immediately useful, simple language, and a good step that should be easy for most Perl programmers.
JavaScript
You’ve probably had some exposure to JavaScript, but go deeper and go functional.
C
You’ve used C for decades under the covers in CPAN modules. So, go write your own CPAN module in native C. And watch how its build crashes when trying to install on most platforms unless they are just so. By learning C, you’ll understand those just-sos. C will be a bit of a trek, but you’ve probably debugged the hardest part about it already: the builds.
Languages you should not learn today
If you weren’t there for these revolutions, don’t bother showing up now. Look instead at a language that is not oversaturated with talented developers or that is on the wane.
Java
If you’re not a seasoned Java developer or planning to work for a body shop like Wipro or Infosys, by the time you don’t suck in Java your friends will have run rings around you careerwise in JavaScript as “full-stack developers.”
Ruby
The Ruby language is declining in popularity, with no bulwark to hold it in place, Ruby will soon go the way of Groovy, a weird cult language (I’ll get the most hate mail for denigrating Groovy, I promise) that isn’t even in the top 50 in terms of popularity.
Groovy
Give it up, people. It is over. Go learn Scala or JavaScript. If a Groovy cultist comes to you, tell him or her you’d rather learn Perl and spell it in all caps to annoy the Perl people.
Perl
Perl too is a weird cult in its own right. It’s been declining in popularity for years, but it remains useful for things that are mainly somewhat-solved problems (I mean: I can just grab code to deal with that mangled CSV file, so why am I writing Perl again?).
Languages newbies should start with
If you know no programming languages, start here with the following languages.
HTML, CSS, and JavaScript
If you are front-end-inclined, learn the languages of the web: HTML, CSS, and JavaScript.
R
Because it is a relatively simple language that can immediately help you with charts and visualizations, R is a good thing to know.
C
Everyone should have a basic understanding of how a computer works. For that purpose, C gets you closer to the metal. It is also one of the most popular languages and will help you in the era of the internet of things.
Bash or PowerShell
Understanding shell scripting is understanding life. It will automate so many mundane tasks for you. Bash is widely useful, while PowerShell is core to the Microsoft ecosystem.
/cdn.vox-cdn.com/uploads/chorus_image/image/59158425/vpavic_180321_2409_0163.0.jpg)